
The INBISCO ISMS is a comprehensive framework that integrates policies, procedures and controls to manage and continuously improve your information security.
NIS2, NIST, NEN7510 and ISO27001 compliant
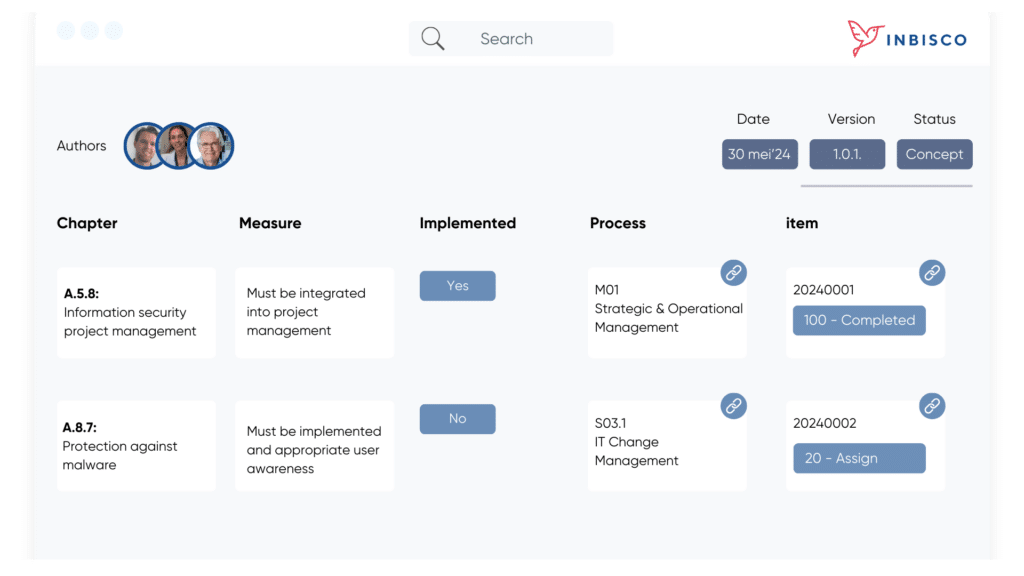
Save a lot of time with the standard ISO27001 framework
Incidents, risks, measures, processes, documents
Link incidents directly to risk treatment plan
In order to protect the continuity of the organization, it is of great importance to have insight into the risks and vulnerabilities of the organization. Set up a clear policy and implement measures to reduce vulnerabilities and risks and to ensure the continuity of the organization.
INBISCO – Secure supports you in this by offering a single system for identifying risks, storing and developing the policy and implementing measures.
The software offers an easy-to-configure rights and roles structure, ideal for organizations with multiple locations. This makes it possible to maintain a consistent quality and safety policy.
These users have insight into all environments within the organization, regardless of location. The data from these different environments is displayed combined, so that a clear picture of the current situation is immediately created.
Business Unit Admins have full access to their own business unit. Within this environment, they can manage all functions and data.
The roles and rights of regular users can be set flexibly. This allows access to be granted at any desired level, depending on the specific needs of the organization.
Yes, the software is so flexible to set up that it is even possible to set the desired language at user level.
INBISCO strives to protect the confidentiality, integrity and availability of information through a risk management process so that stakeholders may have confidence that risks are adequately managed. To achieve this, information security is a key component within INBISCO.
The system is delivered as a SAAS (Software as a Service) solution. Anyone with access to a modern browser (e.g., Microsoft Edge, Google Chrome, Firefox, Safari, etc.) can access the system. In addition to the web application, there is a mobile application for the operating systems iOS and Android. Anyone with a relatively new version of these operating systems on their cell phone or tablet can use the mobile application.
Our infrastructure is continuously monitored, patched and improved in accordance with our infrastructure policy. Want to know more about our information security? Then send a request to [email protected] and we will be happy to share our approach.
ISO 27001 is an international standard for information security. Within this standard it is described how, we as an organization can deal process wise with securing information. To be able to demonstrate that we as an organization handle information securely, we are ISO 27001:2022 certified.
Yes, INBISCO Secure can establish a connection with various login applications for Single Sign-On.